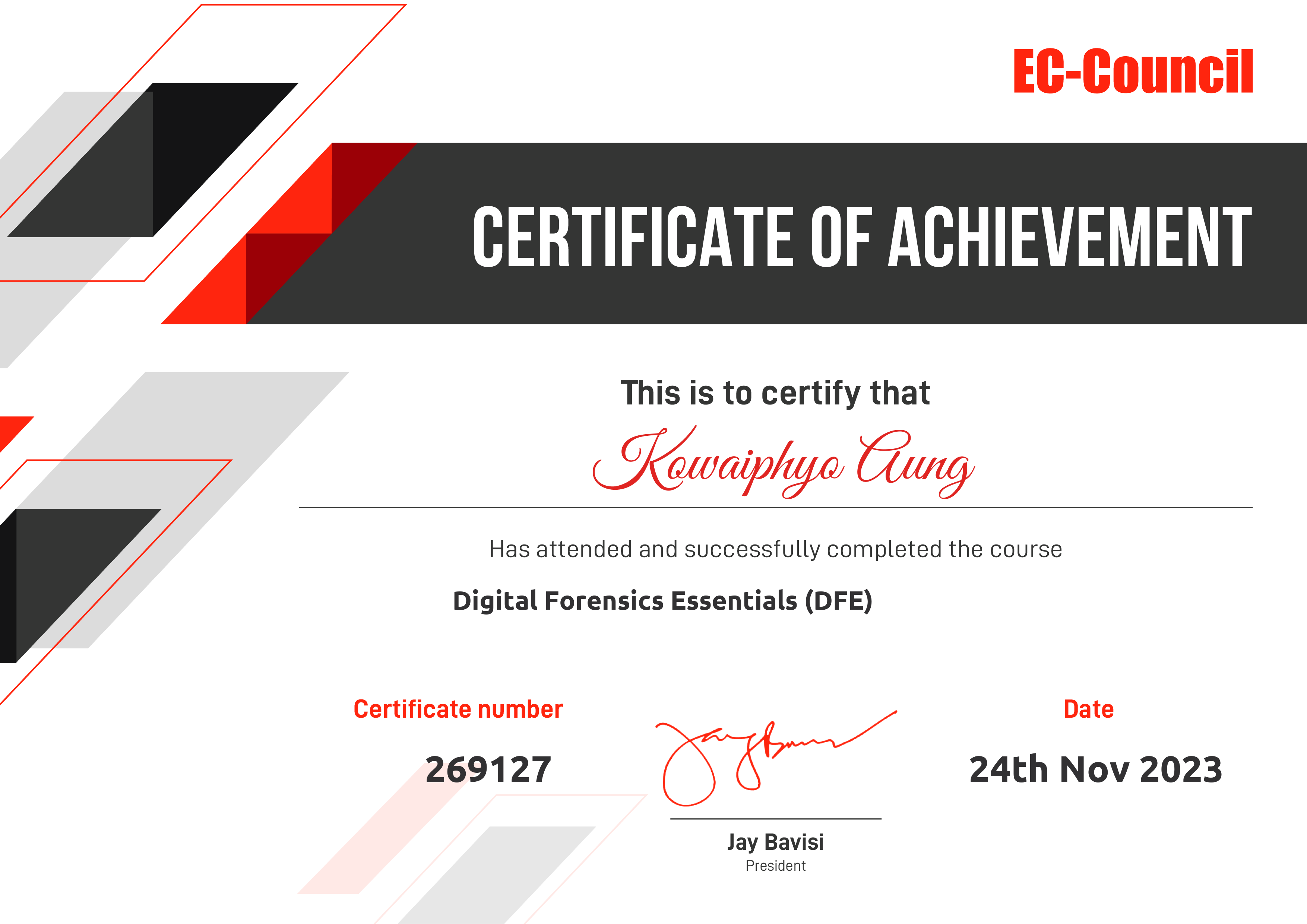
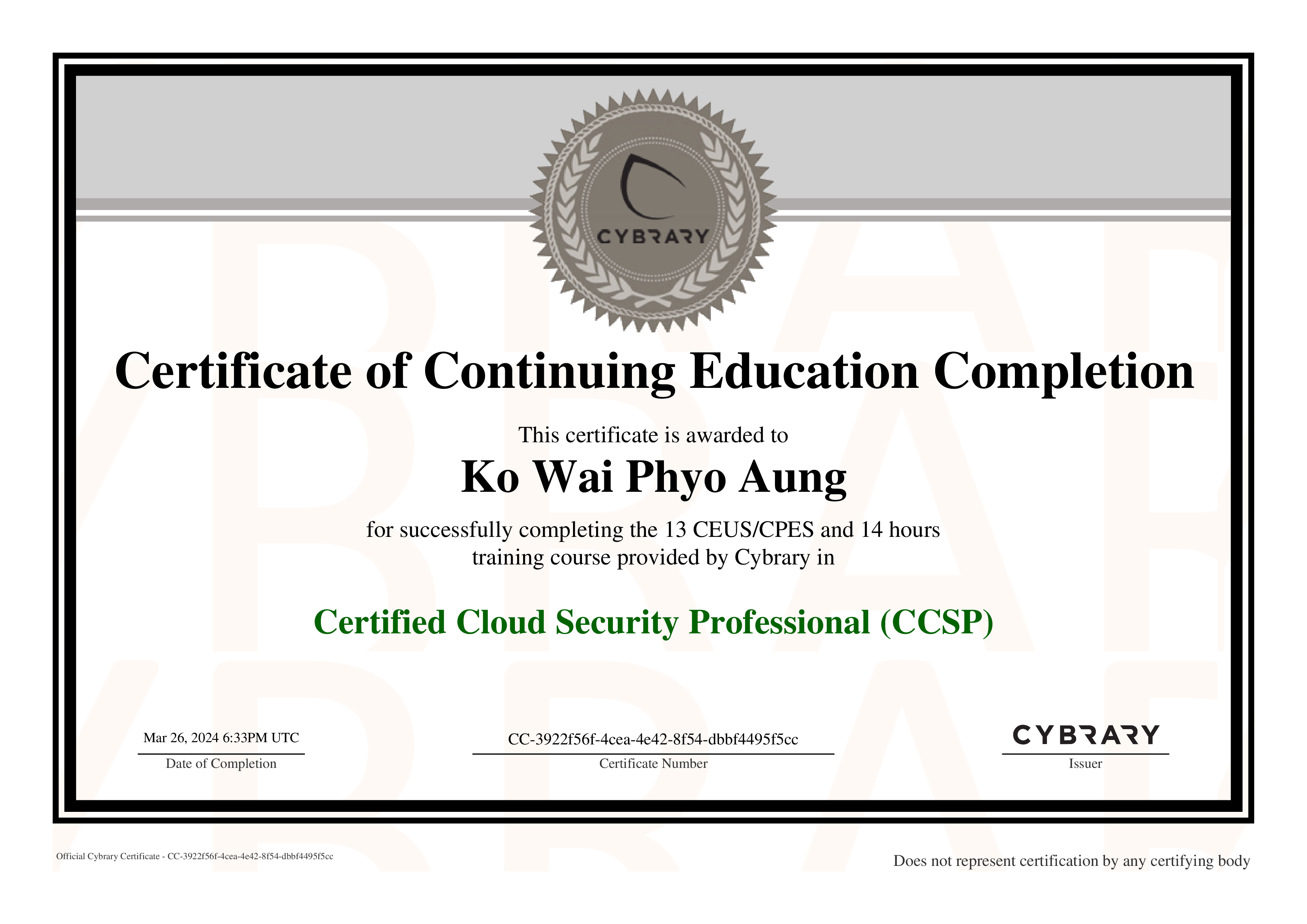
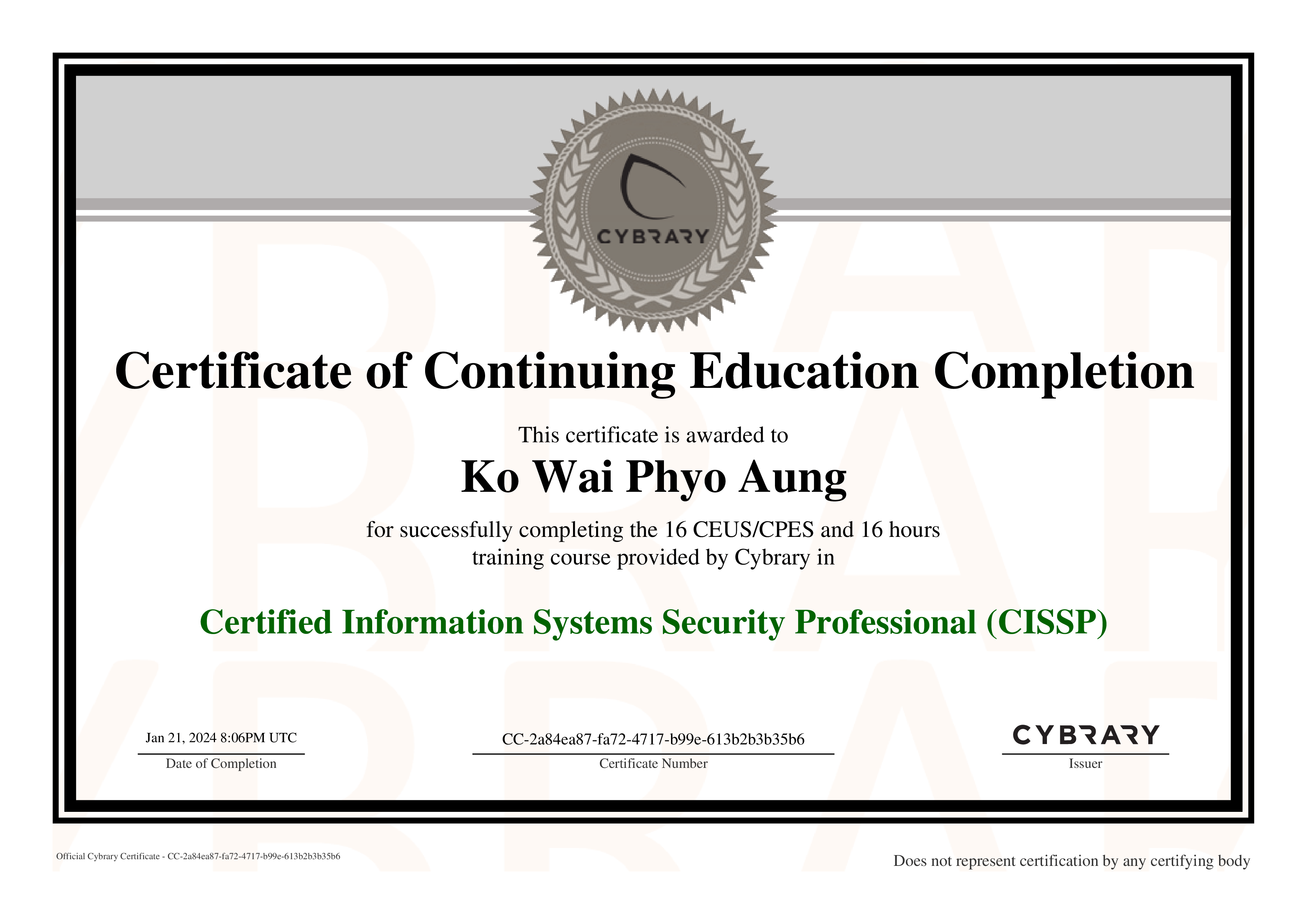
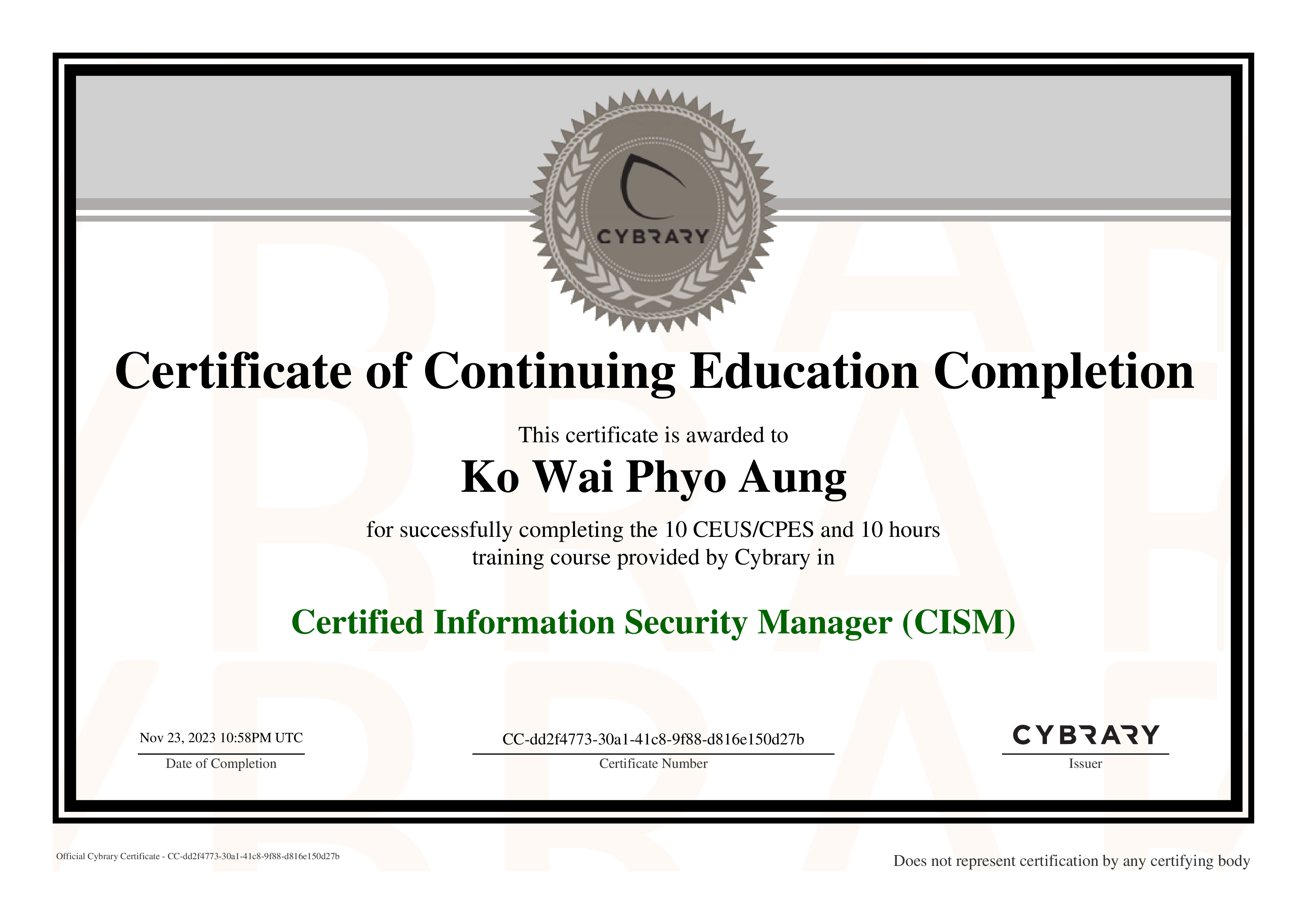
Summary
Sr.Offensive Security Engineer
Experienced and results-driven Senior Offensive Security Engineer with over 5 years of hands-on
experience in designing, implementing, and managing advanced security solutions for cloud environments
and infrastructure. Demonstrates a proven track record of leading cross-functional teams, developing
robust security architectures, and ensuring compliance with industry standards. Adept at conducting
comprehensive risk assessments, implementing effective security controls, and optimizing environments
for maximum security and operational efficiency..
- Cloud Security Architecture
- Identity and Access Management (IAM)
- Threat Detection and Incident Response
- Compliance and Risk Management
- Secure DevOps and CI/CD
- Vulnerability Management
- Data Encryption and Privacy
- Network Security and Firewalls
- Advanced Persistent Threats (APT) Analysis
- Security Information and Event Management (SIEM)
- Endpoint Security
- Security Policy and Procedure Development
- Red Team/Blue Team Exercises
- Penetration Testing
- Forensics and Incident Investigation
- Security Architecture Review
- Threat Intelligence
- Application Security
- Disaster Recovery Planning
- Security Awareness Training
- Cloud Compliance
- API Security
- Security Automation
- Third-Party Risk Management
Education
Bachelor of Science in Computer Science
2010 - 2016
University of Technology (Yatanarpon Cyber City) , Mandalay, Myannmar
Computer science is the study of computers and computer systems, encompassing their physical components
and practical applications. It's an interdisciplinary field that integrates principles from mechanics,
engineering, and logic to explore a diverse array of topics, such as -> Algorithms and data structures ,
Software and hardware design and development , Artificial intelligence , Information , Automation ,
Security , Data analysis , Computational , Theory .
Full Stack - Web Applications Developer
2022 - 2023
MMS One Stop IT Solution, Yangon, Myanmar
A web developer is a professional who specializes in designing, building, and maintaining websites and
web applications. Their primary focus is on the technical aspects of creating functional and user-friendly
websites that meet client or organizational needs. Key responsibilities of a web developer typically
include , Front-End , Back-End , Database , esting and Debugging , Version Control and Deployment
,Security .
C++ Programmer
2020 - 2021
COMPU TECH ICT Institute , MICT Park, Hlaing Township, Yangon.
Studied C++ from 2020-2021 at Computer Technique schools, gaining a strong foundation in object-oriented
programming, algorithm design, debugging, and memory management. Proficient in developing efficient and
high-performance software solutions
Diploma in Cyber Security
2019 - 2020
Alison , Learning Platforms
The risks that cyber threats pose are more common now that we have become almost fully reliant on online
technologies. This diploma course explains how such threats exploit cyber security flaws to cause
financial loss, sensitive data breaches and threats to national security. We discuss the many safeguards
and technologies used to protect computer servers, mobile devices, cloud services and data. Sign up to
master information security.
Professional Experience
Founder - Director
2019 - Current
Cyber Insights Forum - CIF , Yangon ,Myanmar
As the Founder and Director of Cyber Insights Forum (CIF), you will lead the strategic vision and growth
of our cybersecurity company. Your role encompasses setting organizational goals, driving innovation in
cybersecurity solutions, and ensuring the successful delivery of our services. You will oversee all
operational aspects, including team management, client relations, and business development, while
fostering a culture of excellence and collaboration within the company.
- Defining and executing the strategic vision and goals for CIF.
- Leading and managing cross-functional teams to drive company growth and success.
- Overseeing the development and delivery of cybersecurity services and solutions.
- Building and maintaining strong relationships with clients and stakeholders.
- Ensuring high standards of service delivery and client satisfaction.
- Staying abreast of industry trends and technological advancements to drive innovation.
- Managing business operations, including budgeting, resource allocation, and performance evaluation.
Sr.Offensive Security & Cloud Security Engineer
2024 - Current
AyarCloud , Dagon Township ,Myanmar
As a Senior Offensive Security & Cloud Security Engineer, you will play a pivotal role in safeguarding
our cloud infrastructure by proactively identifying vulnerabilities and mitigating risks. You will lead
red team exercises, conduct penetration testing, and collaborate closely with cross-functional teams,
including Network, System, and SOC teams, to enhance security posture. Your expertise in offensive
security strategies, cloud security best practices, and advanced threat analysis will be essential in
developing robust security measures, conducting vulnerability assessments, and driving the overall
security strategy of our cloud environments.
- Leading offensive security operations, including red teaming and penetration testing.
- Securing cloud environments (SaaS, PaaS, IaaS) through rigorous testing and proactive risk management.
- Collaborating with Network, System, and SOC teams to integrate security controls.
- Developing and maintaining security documentation, including threat models and mitigation strategies.
- Staying updated with the latest security trends, threats, and technologies to enhance security
capabilities.
- Led the design and implementation of cloud security strategies for [describe specific projects or
environments].
- Managed IAM policies and roles, ensuring least privilege access across cloud platforms.
- Conducted regular vulnerability assessments and penetration testing, resulting in specific outcomes or
improvements.
- Collaborated with DevOps teams to integrate security into CI/CD pipelines, enhancing application
security posture.
- Implemented security controls for cloud environments, including AWS, Azure, or Google Cloud, to
mitigate risks and achieve compliance.
- Developed incident response plans and led responses to security incidents, reducing mean time to
respond.
Red Team Specialist
2019 - Present
Remote, NCC , New York
- Conducting Advanced Threat Simulations
- Vulnerability Assessment and Exploitation
- Collaboration and Knowledge Sharing
- Continuous Skill Development and Adaptation
Cloud infrastructure Systems Engineer
2024 - Current
One Cloud Technology , Alone Township ,Myanmar
As a Cloud Infrastructure System Engineer, you will be instrumental in designing, implementing, and
managing our cloud infrastructure to ensure robust, scalable, and secure cloud solutions. You will work
closely with cross-functional teams to optimize cloud environments and enhance overall system performance.
Your role involves configuring and maintaining cloud services, managing infrastructure automation, and
ensuring the reliability and security of our cloud resources.
- Designing and deploying scalable and secure cloud infrastructure solutions (SaaS, PaaS, IaaS).
- Managing cloud resources and services to ensure optimal performance and availability.
- Implementing and maintaining infrastructure automation tools and practices.
- Collaborating with development and operations teams to integrate cloud solutions effectively.
- Monitoring and troubleshooting cloud infrastructure issues to ensure reliability and efficiency.
- Staying current with emerging cloud technologies and best practices to drive continuous improvement.
Course Instructor
2022 - Current
MMS IT , Hlaing Township ,Myanmar
As a Course Instructor, you will be responsible for delivering high-quality educational content and
training in cybersecurity and cloud technologies. You will design and develop comprehensive course
materials, conduct engaging and informative classes, and assess student progress to ensure effective
learning outcomes. Your role involves staying updated with the latest industry trends and technologies to
provide relevant and cutting-edge education to students.
- Designing and developing course content, including lectures, labs, and assessments.
- Delivering engaging and informative classes that effectively communicate complex concepts.
- Evaluating student performance and providing constructive feedback to facilitate learning.
- Keeping course materials current with industry standards and emerging technologies.
- Assisting students with queries and providing additional support as needed.
- Continuously improving course content and teaching methods based on student feedback and industry
developments.
Founding Member
2023 - Current
Dev o'Clock , Yangon , Myanmar
As a Founding Member of Dev o'Clock, you will play a critical role in shaping the direction and growth of
our organization. Your responsibilities include contributing to the strategic vision, developing
innovative solutions, and driving the core initiatives of the company. You will collaborate with other
founding members to establish company values, build a strong team, and ensure the successful launch and
evolution of our projects.
- Contributing to the strategic vision and goals of Dev o'Clock.
- Leading and participating in the development of innovative solutions and projects.
- Building and nurturing a high-performing team and fostering a collaborative environment.
- Overseeing key initiatives and ensuring alignment with organizational objectives.
- Engaging with stakeholders and partners to build strong relationships and drive business growth.
- Ensuring the successful implementation and scaling of projects and initiatives.
- Staying informed about industry trends and technological advancements to guide company strategy.
Sr.Cyber Security Instructor
2020 - Current
Gh0st InfoSec Security , New York , United States
As a Senior Cyber Security Instructor at Gh0st InfoSec Security, based in New York, you will be
responsible for leading advanced cybersecurity training and education programs. You will develop and
deliver comprehensive training materials, mentor students, and ensure that participants gain in-depth
knowledge and practical skills in cybersecurity. Your role involves staying at the forefront of
cybersecurity trends and threats to provide cutting-edge education and prepare students for real-world
challenges.
- Designing and delivering advanced cybersecurity training programs and courses.
- Developing high-quality educational materials and practical exercises.
- Mentoring and guiding students to achieve their learning goals and career aspirations.
- Evaluating student performance and providing constructive feedback to enhance learning outcomes.
- Staying updated with the latest cybersecurity trends, tools, and technologies to ensure course
relevancy.
- Collaborating with industry professionals to continuously improve training content and methods.
- Representing Gh0st InfoSec Security at industry events and contributing to the company's thought
leadership.